TEAM 8: JSM Hammer
Spring 2007

@Badwater @Death Valley @winter2006:
left to right - junwei, mingyang, shihong, and one other friend(stone)
MEMBERS
- Jun Wei Chuah
- Shihong Ng
- Ming Yang Koh
PROJECT CONCEPT
- This project will act as deterrence against laptop thefts, providing the owner a greater degree of security.
- The prototype integrates off-the-shelf embedded components, such as motion-sensing accelerometer, buzzer, RFID reader and tags for passive activation of the device and the Tmote Sensor.
MOTIVATION
- A laptop owner today is unable to leave his/her laptop unattended without risk of the laptop being stolen.
- Using our prototype system, an alarm will be activated if the laptop is being handled by unauthorized personnel.
COMPETITIVE ANALYSIS
-
Caveo Anti-Theft PC Card:
- The product works by sensing motion and emitting an alarm when its moved.
- Our product will automatically activate the lock when it does not sense the user’s presence
-
Kensingston Cable Lock:
- The product works by physically locking the laptop to a secure object.
- Our product requires less user input and is a smaller and lighter solution.
TECHNICAL SPECIFICATIONS
Hardware:
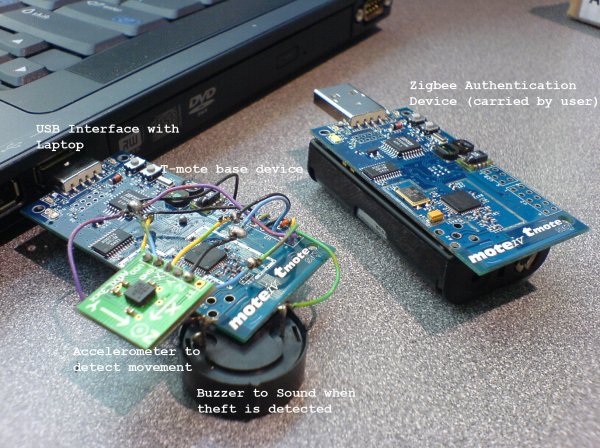
Software:
- Java for laptop application
- TinyOS for Telos Mote
Protocols:
- USB between Telos Mote and laptop
- Zigbee protocol between laptop-side Tmote and keycard Tmote
REQUIREMENTS
- Functional Requirements:
- Detects the presence of the user when in range and disarms the device.
- Arms the device when user is out of range.
- Allows software arming and disarming of device.
- Detects movement of laptop when armed and sounds alarm accordingly.
- Non-functional Requirements:
- Reliability: When armed, the device will detect significant movement and sound the alarm.
- Usability: The device will require minimal user input after installation.
- Threshold: Non-extended small movements will be tolerated by the system.
- Timing: The alarm will trigger within 5 seconds of detection of motion.
ARCHITECTURE
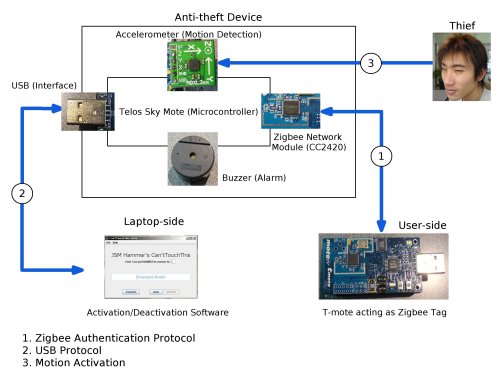
USE CASES (INTERACTION DIAGRAMS)
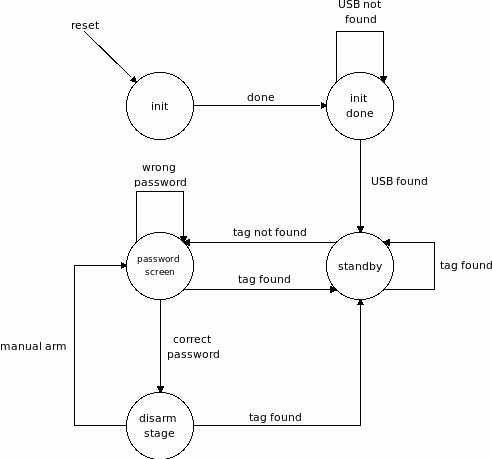
SYSTEM STATES & TRANSITIONS
State Transition Diagram for the laptop software:
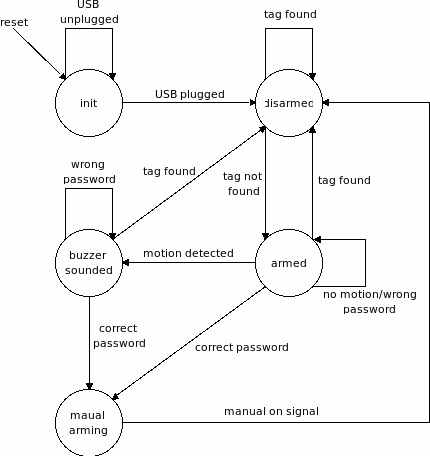
State Transition Diagram for the microcontroller:
RISKS AND MITIGATION STRATEGIES
Risks:
- R1. Compatibility between RFID reader and Telos Motes
- R2. Compatibility between voltage regulator, RFID reader and Telos Motes
- R3. Compatibility of rechargeable battery with rechargeable mechanisms on Telos Motes
- R4. Real-world performance of RFID reader with respect to range
- R5. Constraints with respect to the ports available on Telos Motes
- R6. Difficulty in finding suitable algorithms differentiating significant and non-significant movements
- R7. Usage under different laptop operating environments
Mitigation:
- Worst case usage of Zigbee protocol and Telos Motes for passive device => (R1, R2, R4)
- Requires device to always be plugged into laptop => (R2, R3)
- Usage of 18-348 board to meet specific port requirements => (R5)
- Usage of multiplexers to meet port requirements => (R5)
- For worst case, any slight movement would trigger alarm => (R6)
- Requires Windows as main Operating System => (R7)
ERROR HANDLING
-
Used hysteresis to minimize sensitivity of device
- Range of 1.5 feet for arming
- Range of 16 feet for disarming
-
Kept track of the movements over time
- To minimize alarm sounding off due to accidental movement
- Alarm sounds only if significant movement detected over a certain time range
IMPLEMENTATION DETAILS
-
Java Application:
- Developed using Eclipse
- Uses the RXTX library to send and receive data from the tmote.
- Receives a TOSmsg from the tmote, but sends individual bytes to the tmote
-
TinyOS code in laptop side tomote:
-
TinyOS code for tmote to receive msg from laptop
- Used the interface genericComm
- 1 byte sent at a time
- Byte sent indicates the user’s choice of arm or disarm
-
TinyOS code for tmote to send msg to laptop
- Implements the interface SendMsg to send a TOSMsg packet to the laptop
- Analyzes the degree of movement
- Sends a msg to laptop if movement is significant
-
TinyOS code for tmote to receive msg from 2nd tmote
- Implements interface ReceiveMsg to receive a TOSMsg packet
- Verifies that the packet is correct by checking moteID of the packet
- Uses the tosmsg->str component to check for the strength of the signal received
TEST CASES
- Startup (Devices start up without errors)
- User moves laptop (Nothing should happen)
- User leaves laptop (Arming of device)
- Thief moves laptop (Alarm rings)
- User returns to laptop (Disarming of device)
- Shutdown (Devices shutdown properly)
EXPERIMENTAL EVALUATION
- Metrics:
- Range of T-motes:
- Sets distance at which we arm and disarm the t-mote
- Degree of movement of accelerometer:
- Sets the degree movement to trigger off alarm
- How to measure:
-Conducted 40 trials for each metric:
- Measured # times in which device is constantly being armed/disarmed for 5 seconds at a particular distance
- Measured # times in which alarm is sounded at the various movements
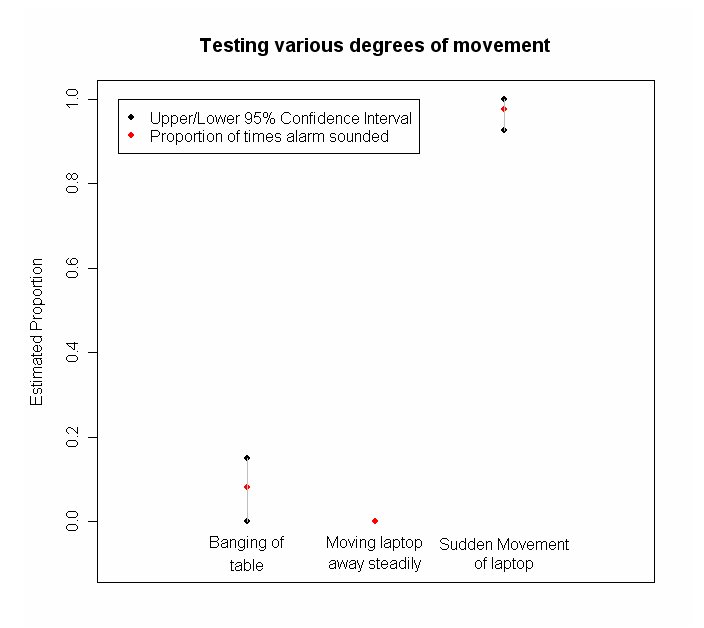
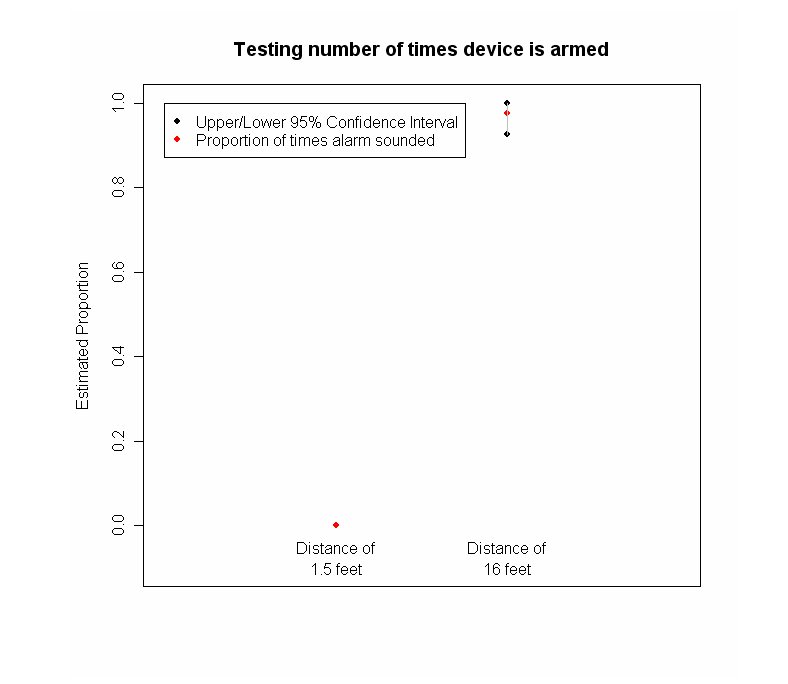
- Initial experimental results: 10 April 07
,
- Almost every sudden movement would cause alarm to ring
- Thief can steal laptop by moving it away slowly
- Banging of lab table does not cause alarm to sound off most of the times
- Device will be in disarm mode constantly if user within 1.5 feet
- Device will likely be in arm mode constantly if user is at 16 feet from device
LESSONS LEARNED
- Subtleties in tinyOS: Deluge library prevented buttons from working
- Subtleties in tinyOS: Using genericComm instead of which hpluart to send packets
- Subtleties in tinyOS: Using Tosmsg->strength instead of Tosmsg->lqi
- RFID voltage incompatibility: Leads to complications when using it with tmote
- Accelerometer detects only acceleration, slow movement escapes detection
- Tmote to tmote communication strength varies greatly
FUN STUFF
-
why JSM Hammer? aha. We are inspired by MC Hammer's You Can't Touch This; During a Concepts of Math lecture with Prof Mackey, some student was asking what should we do with that term in expression. And he flatpans: "to quote the late MC Hammer.... You Can't Touch This". And of course, JSM stands for Junwei Shihong Mingyang, in order of weight.
-
why an anti-theft device? aha. This idea was conspired a few months after one of our friend's house got looted and the thieves stole several laptops. Wouldn't it be nice to have an irremovable and annoying alarm with the laptop that will sound off when a thief tries to getaway with it?
-
during testing for our testing, there is one test that requires us to ensure that non-malicious motion detected should not be registered for raising the alarm. Then Shihong came up with the bright idea of banging the table. In the end, Shihong spent the next 2 hours banging the table to test if the alarm will sound off.
REFERENCES
- Project Proposal and Requirements,
Team Project Presentation, January 31, 2007
- Design & Architecture,
Team Project Presentation, February 16, 2007
- Mid-semester Project Status,
Team Project Presentation - Demo Video, March 2, 2007
- Test Plan & Experimental Validation
Team Project Presentation, March 28, 2007
- What's Done, What's Left
Team Project Presentation, April 11, 2007
- Final Project Presentation,
Team Project Presentation, Date TBD
- Project Poster,
May 4, 2007
Back to the top of this page
18-549 course home page





