This week I wrote the Host Card Emulation portion for the phone app. Because the HCE is designed to work no matter what application is open, the HCE is implemented as a Service that runs when APDU (Application Protocol Data Unit) is detected (basically detect when reader is trying to talk with the phone). To register the Service class, the application Manifest (ApplicationManifest.xml, XML file containing various information about the application and its context) needs to be updated with the Service and its NFC permissions. An Intent Filter is added in the manifest so the phone knows to run the service when APDU detected from reader. Also, a new XML file containing APDU specific information is added, and the Service is updated to route to this new XML file, dubbed apduservice.xml. The most important information in this file is the AID filter (Application ID), which is basically information that the reader must send and the app must have to know what to run when communicating. Finally, a class extending the HostApduService class made specifically for APDU was created. This class defines functions to process APDUs, which is basically a byte stream decoder. To process an APDU, I needed to look at sets of bytes in the APDU, which has various data fields. The format for APDU is defined, so I just needed to check indices of the APDU, which is a byte[] (byte array) as exposed by the HostApduService interface. Finally, another byte[] is returned from this function as a response, but I have not yet implemented what this byte [] will be. It should be secure and unique. UID (NFC) should not be used because another NFC tag could easily mimic the same UID. The security options should include some phone specific unique token, possible distributed by the server. I am looking into several security options, but this should be work for next week. For the near future (Sunday, Monday, and Tuesday), I am working on getting the NFC Reader code and this code to communicate correctly.
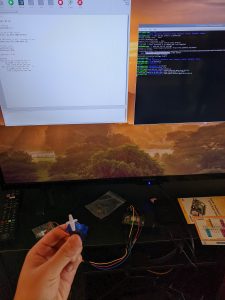
I also worked on wiring the Raspberry Pi and the NFC reader, which was work planned for next week. This portion was fairly straightforward, but required some time to debug some hardware specific components. I also tested the NFC reader with both a smart card and an Android phone using a downloaded tool that reads bytes from i2c pins. The NFC + RPi interface worked for both the smartcard and the Android.
I also started on writing the NFC reader code, which needs to precisely send the APDU to the phone, and respect the protocols needed (ISO…). There isn’t a lot of information about this online, so I am basically just testing by trial and error. For example, the mentioned AID filter needs to include a first byte that defines what type of AID it is. Online example use “registered” AIDs, instead of proprietary ones that don’t need registration. If they use registered AIDs, then won’t another application with the same AID be problematic because they are both defined to have the same AID filter on the Android phone? Thus I will probably need to define my own “proprietary” AID. I am still fairly confused about this, so I will work to understand and implement this portion of the reader tomorrow.
I believe by next week, I will have working reader and phone code, and I will implement the security for the reader/phone. The security should simply be some overhead for each component, so it should not take that long. After this work is finished, the following week will be working on the UI features for the phone app (HCE is more like a background service). This will include simple features like registering a lock (will probably work with Michael on that). This will not take more than a few days because I did sufficient learning on basic Android App Development in the previous week, and already have basic XML layouts. I will be done with my portion of the project then, so will help out on other portions or continue to improve my portion of the project.
Based on the Gantt Chart, I am on task. Some of the tasks are currently being done concurrently, so the schedule may be slightly off for some of the tasks. This is because I need to develop each component at the same time to get a better understanding of the tools and frameworks surrounding the whole system. Also, being able to test the components is necessary.

Sorry for the image quality. Here, a tool called nfc-poll is being used to detect NFC reader input. The NFC reader had to be registered in the Raspberry Pi config (I2C), then running this tool allowed for the UID, ATQA, and SAK to be read (NFC specific information). The text is blurry but I ran the tool twice to check if the smartcard had the same UID to make sure the NFC was working correctly. I also tested with the smartphone when we were working as a team earlier, but I forgot to take a photo.